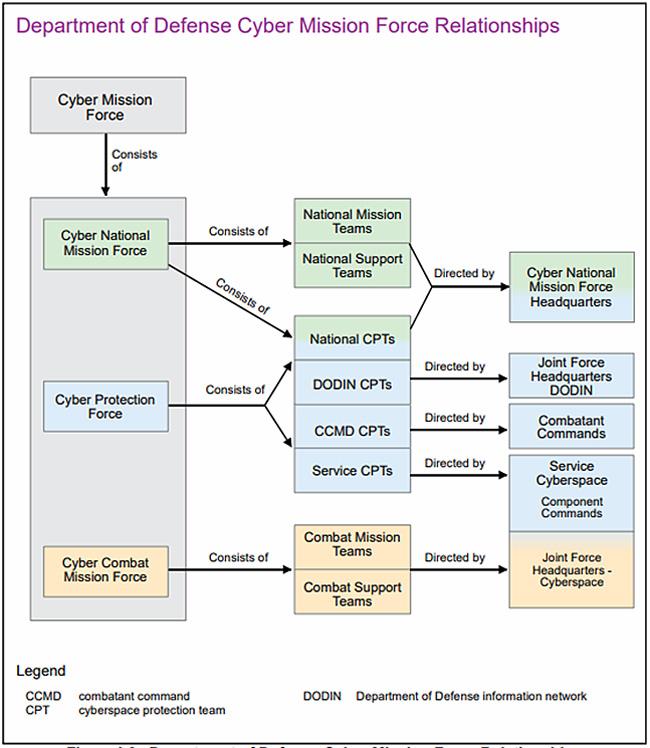
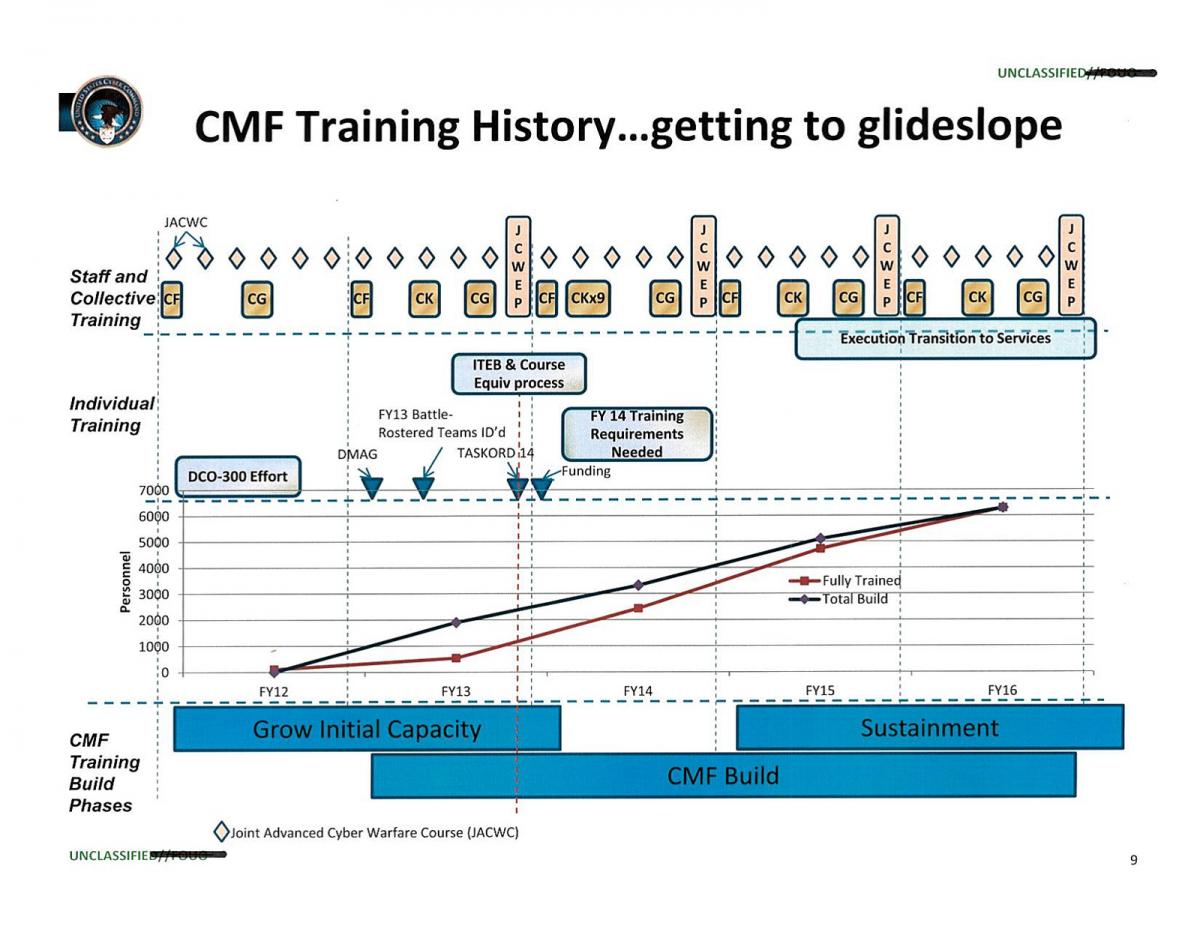
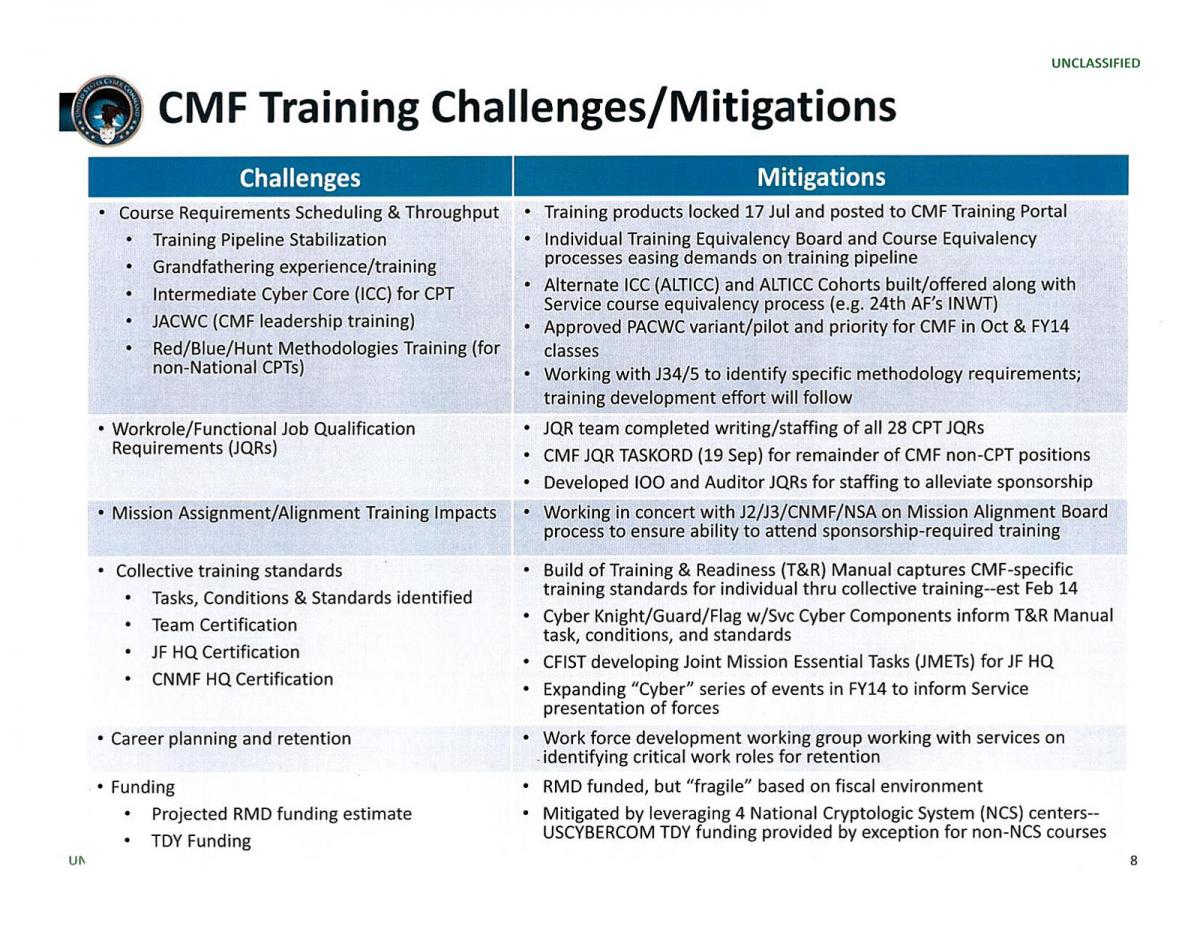
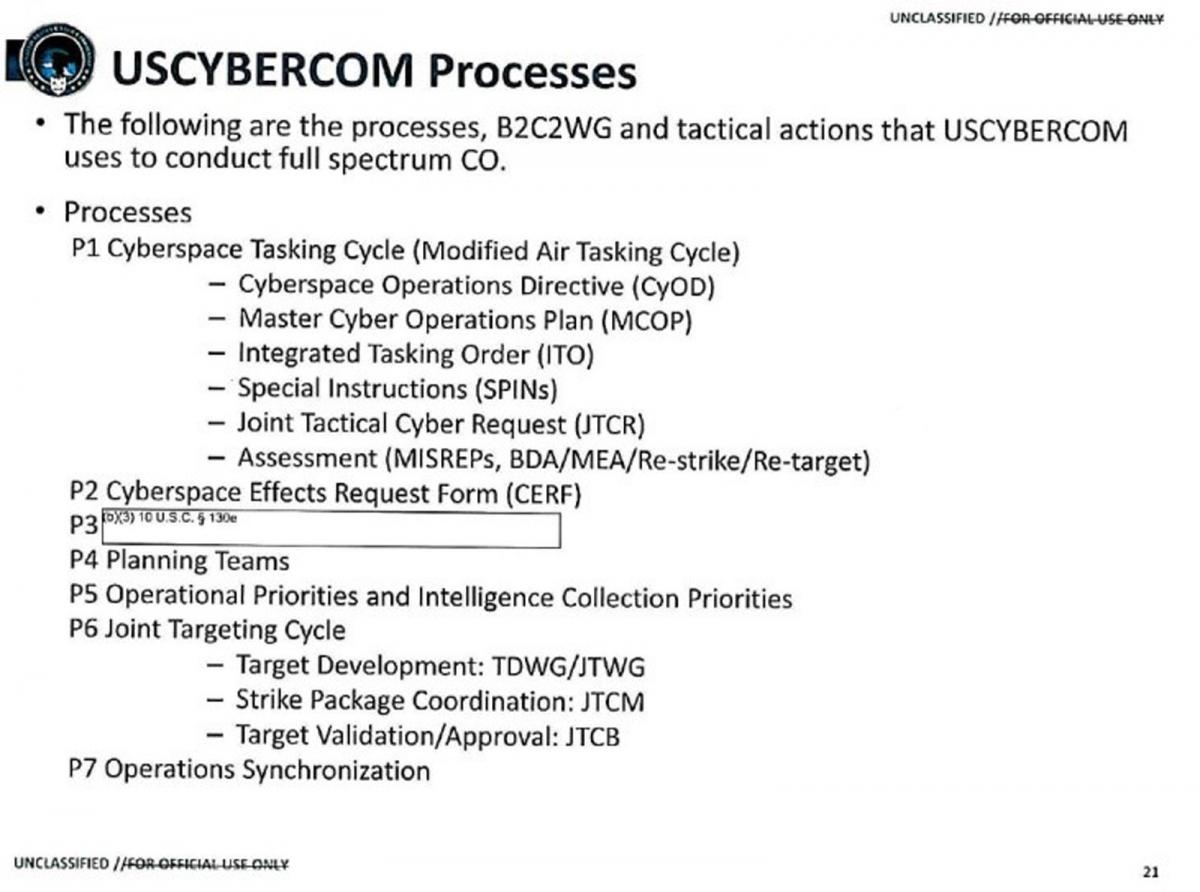
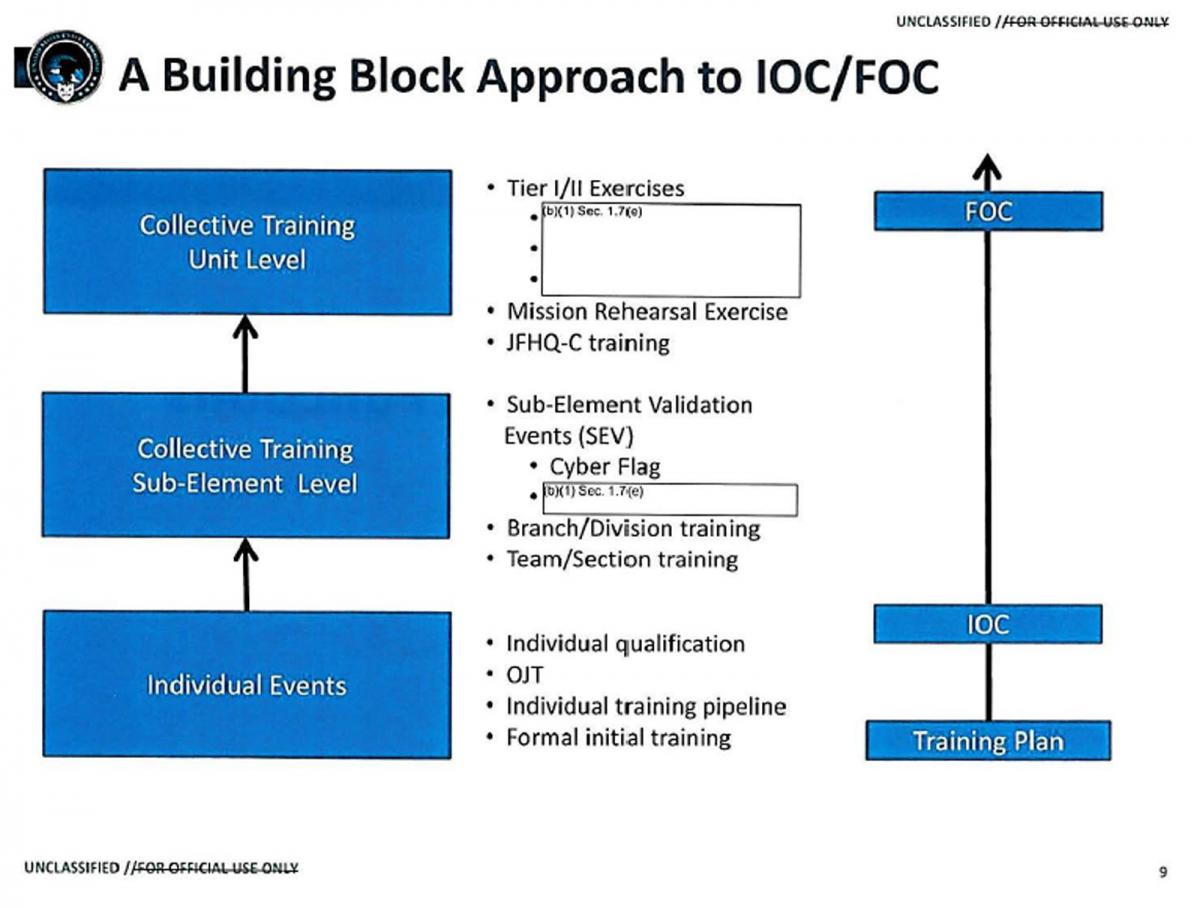
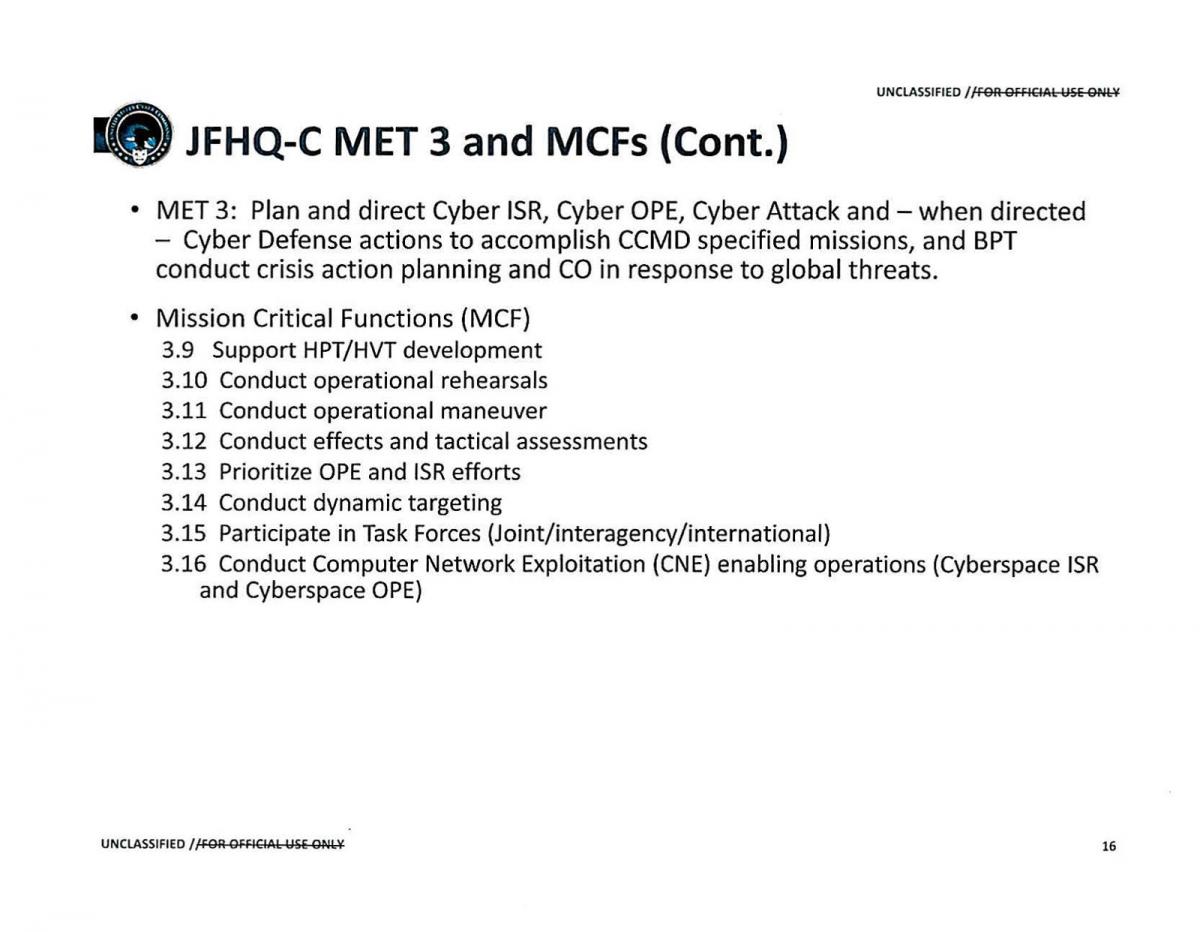
Evolution of Cyber Mission Force and Joint Force Headquarters – Cyber portrayed in annual orders to build the force
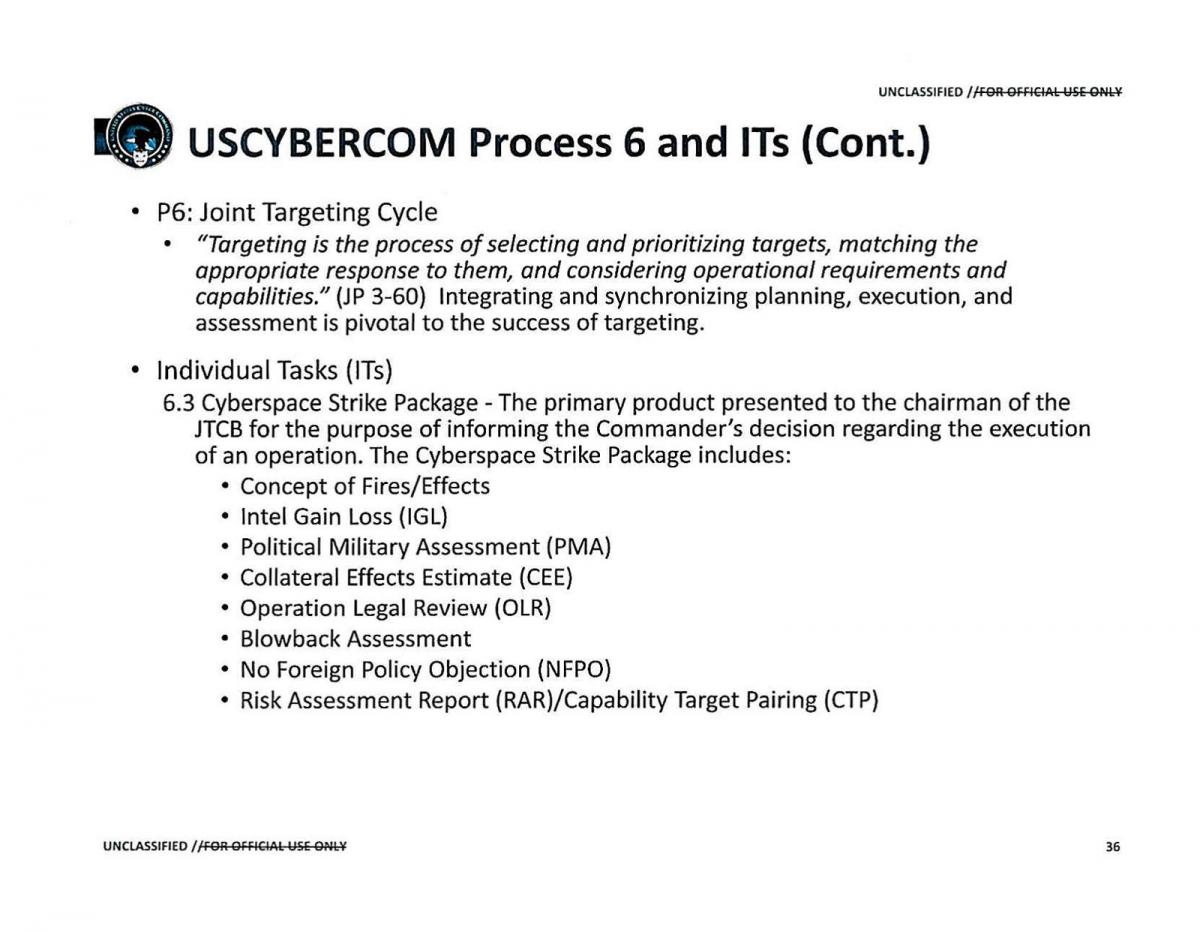
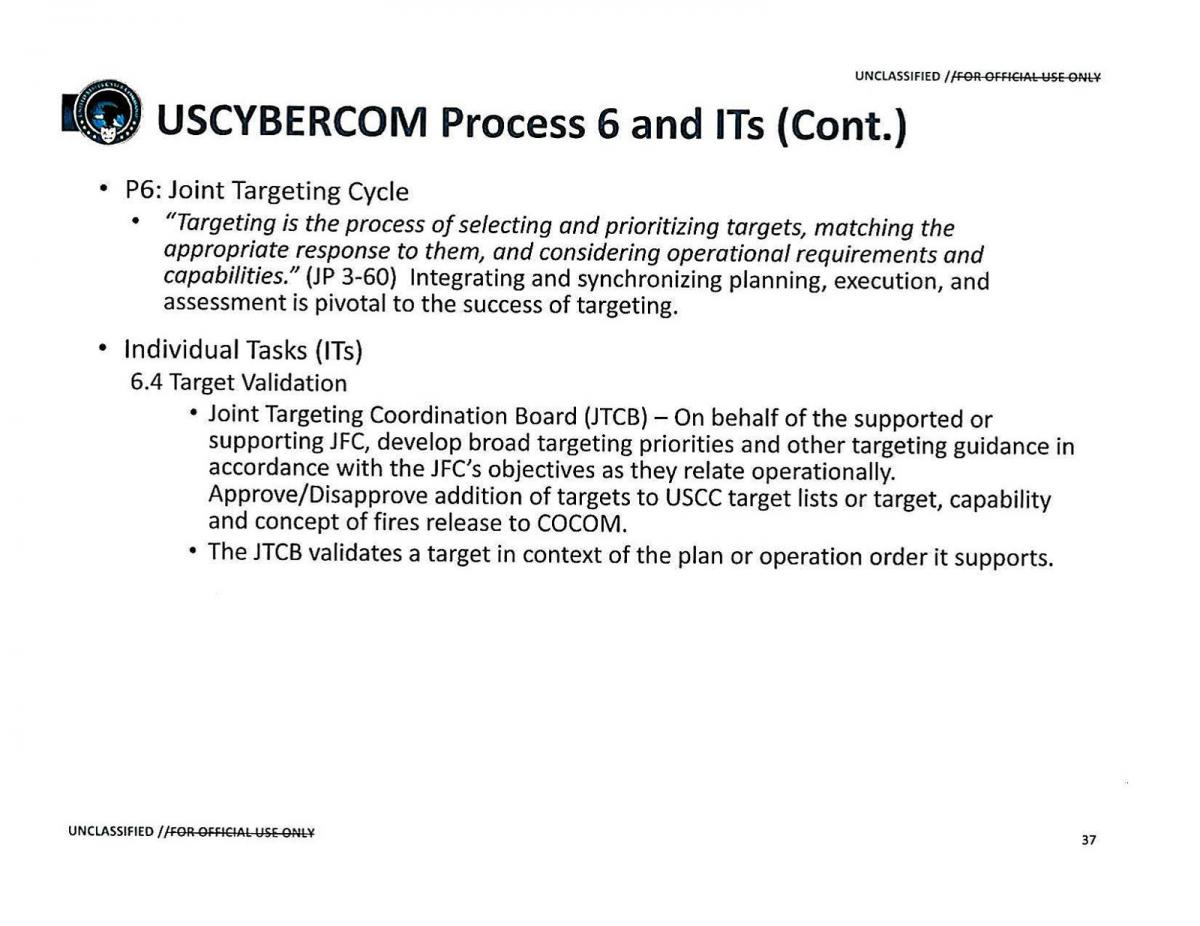
Declassified documents give insight into USCYBERCOM Mission Essential Tasks and Operational Processes
Briefing slide reveals impact of 2013 government shutdown on USCYBERCOM training and development
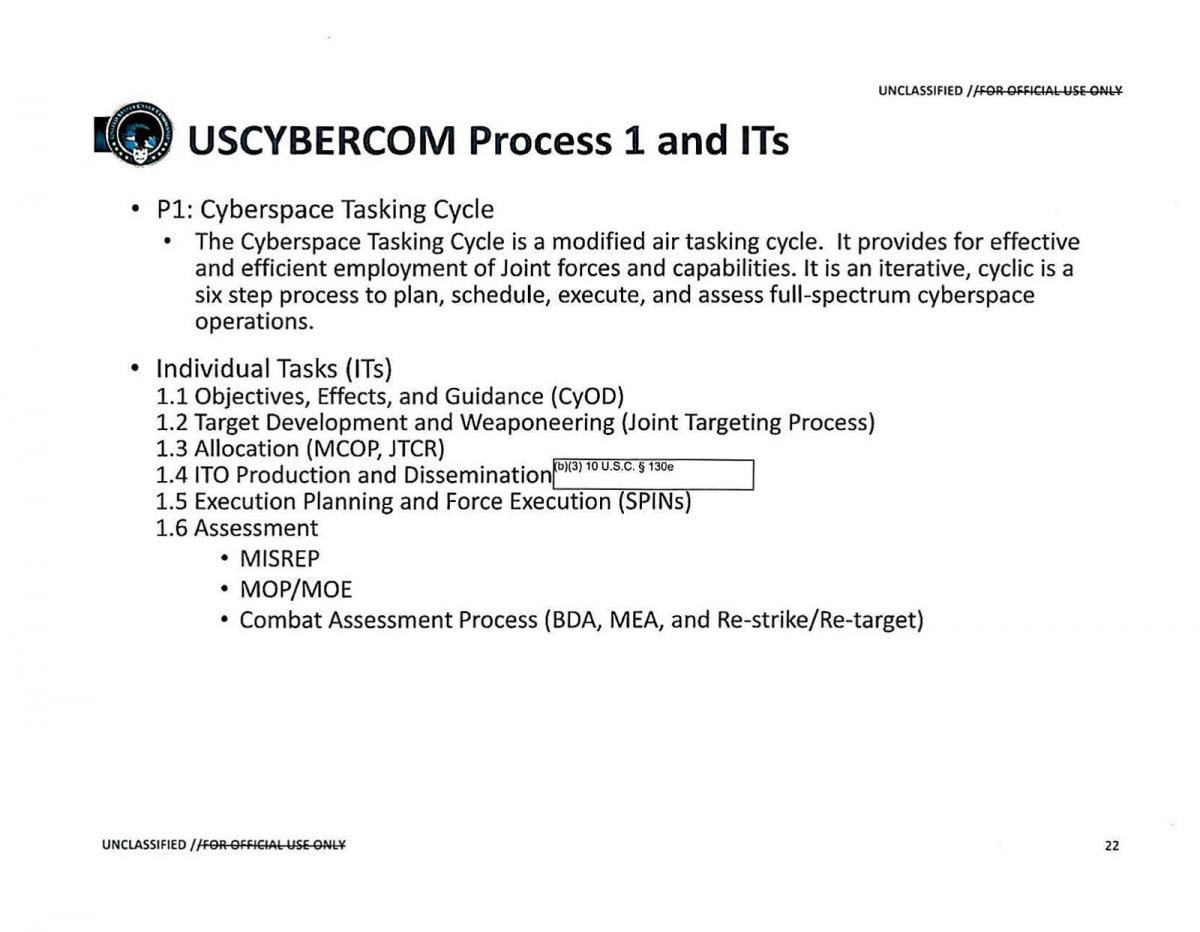
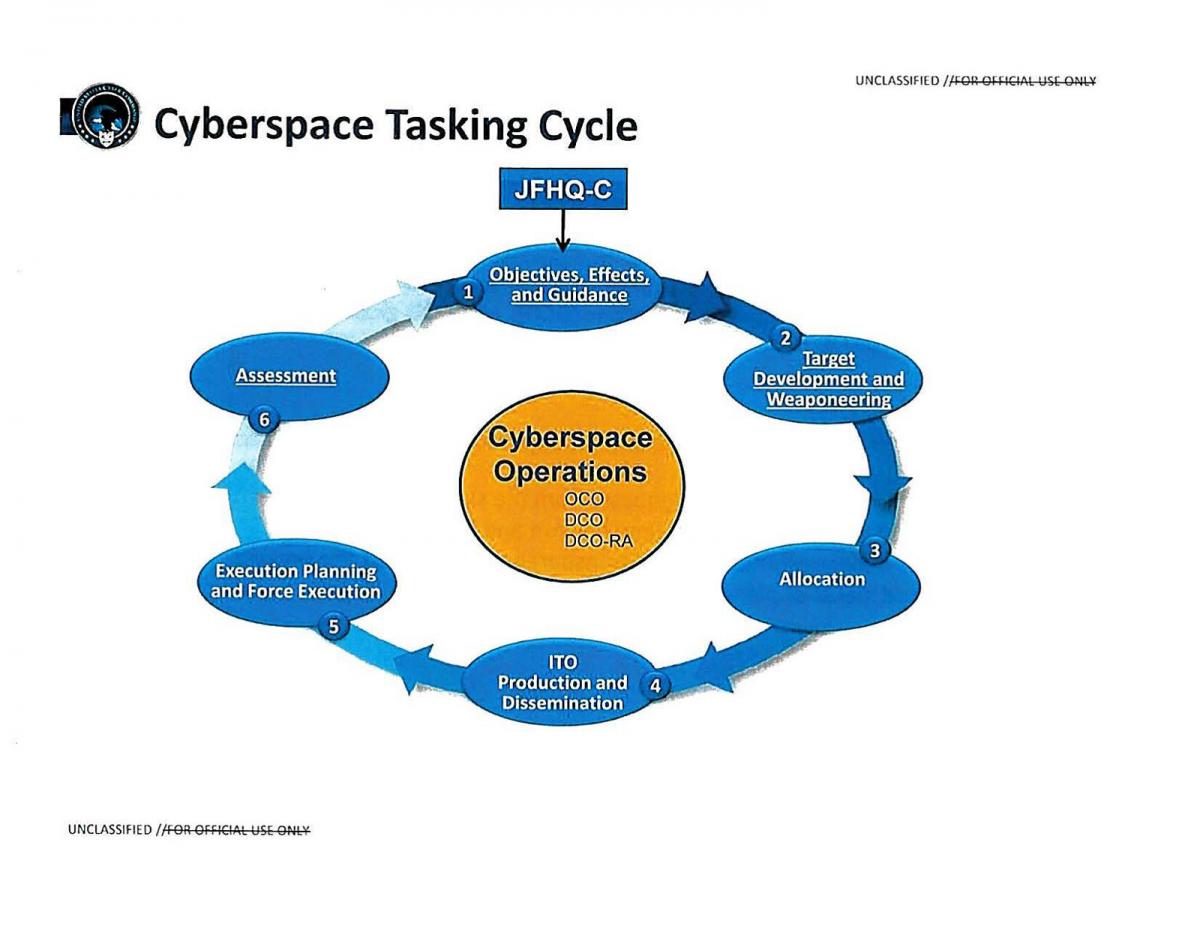
US Military Cyberspace Tasking Cycle adapted from air operations; cyber operations adhere to joint targeting doctrine
OIG Report suggests development process outpaced strategic planning