Washington, D.C., June 29, 2019 – After a series of events starting in the late 1980s gradually awakened the US Department of Defense to the seriousness of threats to computer networks, the US military assembled the first joint task force explicitly formed around the concept of cyber warfare. Twenty years ago this month, Joint Task Force – Computer Network Defense reached full operational capability.
Documents donated by Jason Healey of Columbia University and cyber historian Karl Grindal, published today by the National Security Archive, contain the challenges, concerns, and strategies of those involved in this stage of the US military’s cyber-warfighting development.
* * * * *
In the late 1990s the United States’ Department of Defense rapidly created an organization that, after several evolutions, would become a part of today’s Cyber Command (USCYBERCOM). This process began after two main events, Eligible Receiver and Solar Sunrise [Document 8], served as wake-up calls for the military. The 1997 Eligible Receiver exercise raised issues about the lack of DoD coordination in responding to attacks on computer networks and uncertainty over the legal authorities concerned. Challenges in responding to the real-life computer network attack code-named Solar Sunrise in early 1998 confirmed these findings and drove home the need to establish a response mechanism for such events [Document 5].
Two possibilities were then considered as interim solutions [Document 3]. The first was an expansion of the Joint Command and Control Warfare Center (JC2WC) headquartered at Lackland Air Force Base near San Antonio. Though this option was recommended by the Service Operations Deputies (OPSDEPS), the Joint Chiefs ultimately settled on the second option. This resulted in Joint Task Force – Computer Network Defense (JTF-CND) being co-located with the Defense Information Services Agency (DISA, a combat support entity previously known as the Defense Communications Agency) in the National Capital Area.
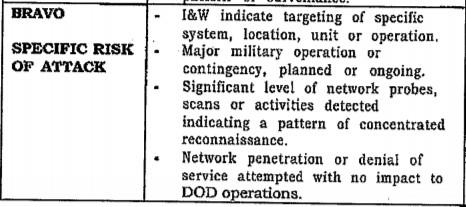
By October of 1998 the plans for JTF-CND were nearly complete after disagreements over the integration of law enforcement and criminal investigation elements were settled. There was resistance from the Navy over the automatic delegation of JTF-CND authority over the systems of any forces set at INFOCON (INFOrmation CONdition) Bravo [Document 5], a move intended to centralize DOD response to computer attacks but with the potential to further complicate the other tasks of the attacked force. A unit was to be set to INFOCON Bravo if it the situation met the following criteria:
[Document 12] Note: I&W means “Indicators and Warning”
The Navy also objected to Air Force dominance over the joint task force’s leadership positions [Document 5]. The initial draft of JTF-CND’s charter gave both command and deputy command slots to Air Force officers. The Navy proposed language specifying the top two positions be from different services. By the end of 1998 [Document 7] the final organization chart for JTF-CND’s command had been settled, and each service was in the process of deciding on its own respective contributions. Additionally, and as a result of changes to the DOD’s Unified Command Plan (UCP), JTF-CND was expected to be transferred to US Space Command (USSPACECOM). Talking points [Document 12] written in March 1999 confirm the Joint Chiefs’ plan to assign JTF-CND to US Space Command (a precursor to STRATCOM under which CYBERCOM would eventually grow). This plan did not involve relocation, however. JTF-CND was to remain at DISA.
A presentation [Document 14] on JTF-CND given to the Defense Science Board in early 2000 speaks to how far the mission of computer network defense had progressed. A clearer vision of the threat in cyberspace is presented with an explanation as to how computer network defense fit into the U.S. military’s overall mission. The organizational charts of the five component contributions (the three services, The Marines, and DISA) are outlined in this presentation, revealing an apparent lack of uniformity between components. The presentation also served as an education on how JTF-CND viewed the cybersecurity landscape, including a ‘generation’ model of threat sophistication seemingly borrowed from the system for categorizing fighter aircraft.
At the end of 1999 JTF-CND became Joint Task Force – Computer Network Operations (JTF-CNO) and the following year was put under the control of USSPACECOM, which was in turn dissolved into USSTRATCOM in 2002. In 2004 [Document 17] the mission of JTF-CNO was rolled into JTF-Global Network Operations (JTF-GNO). Several organizations, including both JTF-GNO and DISA as well as the Joint Functional Component Command for Network Warfare (JFCC-NW), were reorganized under CYBERCOM and moved to Fort Meade in 2010. [USCYBERCOM history: https://www.cybercom.mil/About/History/]
The progression of USCYBERCOM’s evolution is critical to comprehending United States cyber strategy. Understanding the components that would eventually form the US military’s primary tool for operations in cyberspace generates insight into the institution playing one of the more critical and secretive roles in US national security.
Documents
Document 8
Joint Chiefs of Staff, “Eligible Receiver 97 and Solar Sunrise”, 1999. Unclassified.
Document 10
US Air Force, “Information Assurance Update”, January 29 1999. Unclassified.