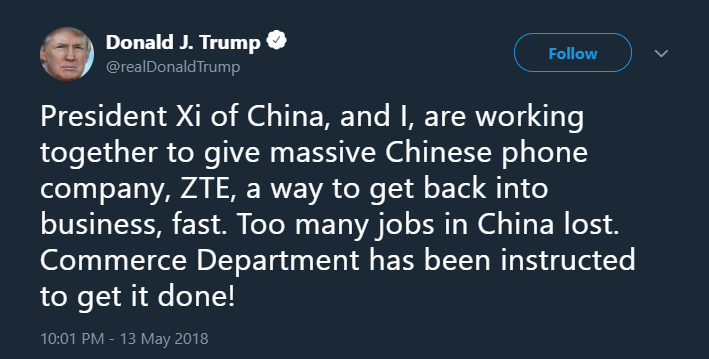
On May 13, President Trump announced on Twitter that he was working with President Xi Jinping of China to assist the Chinese telecommunications company ZTE. This announcement surprised many in the national security community as the US Government has in the past claimed that devices made by ZTE, as well as other Chinese telecom firms such as Huawei, are used by the Chinese Government to conduct surveillance.
This week’s Cyber Brief adds to the Cyber Vault an investigation into Huawei and ZTE published by members of the House Permanent Select Committee on Intelligence, a report by the US-China Economic and Security Review Commission on China’s telecom sector, a 2011 DoD report on China including information on China’s cyber capabilities and technical development, and a bill introduced in the House earlier this year which would ban Federal agencies from using ZTE and Huawei goods and services.
The Brief also highlights a collection of documents from the Vault concerning China’s broader capabilities in cyberspace.
New to the Cyber Vault

Document 01
This edition of an annual report to Congress covers all aspects of Chinese military and security including cyber and telecommunications. This report is specifically referenced in HR 4747 introduced in the House of Representatives January 2018.

Document 02
This document reports the findings of research into Chinese telecommunication investment and its implications for communications products, infrastructure, and supply chains.

Document 03
This document reports the findings of an investigation into the counterintelligence and security threat posed by Chinese telecommunications companies operating in the United States.

Document 04
This bill introduced in the House of Representatives would prohibit the Federal Government from using the products and services of ZTE and Huawei.
From the Vault
This study, prepared for the U.S.-China Economic and Security Review Commission, focuses largely on Chinese computer network exploitation (CNE) as a strategic intelligence collection tool. It examines Chinese CNE operations strategy and operations during conflict, key entities in Chinese computer network operations, cyber-espionage, an operational profile of an advanced cyber intrusion, and a chronology of alleged Chinese computer network exploitation events.
This report, prepared for the U.S.-China Economic and Security Review Commission, focuses on six topics: information warfare strategy, Chinese use of network warfare against the United States, key entities and institutions supporting Chinese computer network operations (the Third and Fourth Departments of the Peoples Liberation Army's General Staff Department), potential risks to the U.S. telecommunications supply chain, the comparison between criminal and state-sponsored network exploitation, and the risks and reality of collaboration between U.S. and Chinese information security firms.
This research paper examines the growth of Chinese cyber capabilities - including those for offensive, defensive, and computer network exploitation operations. It also compares China's capacity and potential in cyberspace to United States efforts with regard to cybersecurity. In addition, the author suggests a number of steps to improve U.S. cybersecurity policy.
Threat Connect, Camera Shy: Closing the Aperture on China's Unit 78020, 2015. Not classified.
This private sector study of a Chinese cyber intelligence unit examines the techniques employed, targets throughout Southeast Asia, and the unit's focus on the South China Sea, "where China's increasingly aggressive assertion of its territorial claims has been accompanied by high-tempo intelligence gathering."